Feedback, In this issue, Issue 21/2024
(Cyber)water health security
For a (non-)IT professional or (non-)pentester, the approach to cyber-security in the context of water health security seems to be a pretty much abstract concept. While there are reports from time to time in the media about attempted attacks (or successful attacks) on water supply systems, a closer look at the subject from the point of view of an environmental engineer has always seemed to me to be beyond competence. And here comes the first question – is cyber security in water utilities (and not only) exclusive to IT/automation/monitoring/control departments, etc.? Nothing could be further from the truth.
The critical and important role of the water and sewer industry in cybersecurity
Currently, we are seeing a feverish preparation of the water industry (as one of the key sectors – but more on that below) for the requirements of the new EU directive on cyber security, and a veritable rash of solutions to adapt to the new requirements.
How to approach it?
Directive (EU) 2022/2555 of the European Parliament and of the Council of December 14, 2022 on measures for a high common level of cyber-security within the Union (the so-called NIS 2 Directive) entered into force last January and replaced Regulation (EU) No. 910/2014 and Directive (EU ) 2018/1972 and Directive (EU) 2016/1148. The document primarily aims to harmonize across the Community the requirements and level of security in cyberspace, control of the indicated risks and cooperation in this regard.
Exactly on October 17, 2024, the deadline for transposing EU regulations into national law passed. The draft amendment to the Law on the National Cyber Security System (NSC) and Certain Other Laws (hereafter referred to as the draft) is currently undergoing an intensive process of adoption. The document (dated October 3, 2024) is already after consultations and, according to assumptions, is expected to be adopted later this year by the Council of Ministers and finally enacted at the beginning of 2025. It should be mentioned that the current law on the National Cyber Security System has been in force since August 2018.
What to use to implement safety rules?
A set of important guidelines for maintaining cybersecurity, for both public and private entities, is the National Cyber Security Standards (NSC). The study contains recommended solutions for maintaining the security of networks and information systems. The indicated guidelines have been prepared based on the US National Institute of Science and Technology (NIST) standards and appropriately referenced to the realities of national law (as of the date of preparation), and apply to entities of the national cyber security system, including key service operators.
The aforementioned guide fulfills the state’s commitment to develop and implement National Cyber Security Standards, stemming from the Cyber Security Strategy 2019-2024. The guidelines provide valuable suggestions and guidance, including on selecting solutions, planning for emergencies, and managing cloud accesses. The NSC cites confidentiality, integrity and availability as the main attributes of cyber security. These standards are subject to successive reviews and updates. At this point, it is worth mentioning that on October 28, 2024, a draft of Poland’s Digitization Strategy for the next 10 years was presented by the Ministry of Digitization. One of its priorities is cybersecurity in the broadest sense, including with the use of AI. The document has been sent for public consultation, where comments can be submitted until December 10, 2024.
In relating cyber security requirements to the water sector, which makes extensive use of industrial networks (e.g., SCADA-type software), equipment controllers, etc., it is useful to use the international series of standardsIEC 62443, which specifies requirements for threat prevention for both users and solution providers and integrators. Minimum standards for information security are indicated by the ISO/IEC 27001 standard.
In this article we will focus on the challenges that water utilities will face after the implementation of the NIS 2 Directive into national law, that is, after the implementation of the update to the NSC Law. The document presented here introduces many changes and will very much affect the operations of the water supply sector.
For starters, it implements a self-identification mechanism by key or important entities. According to the draft law, a key entity is a natural person, a legal person or an unincorporated organizational unit indicated in Annex 1 to the Law, which exceeds the requirements for a medium-sized enterprise set forth in Art. 2 paragraph. 1 of Annex I to Commission Regulation (EU) No. 651/2014 of June 17, 2014 declaring certain types of aid compatible with the internal market in application of Article 107 and 108 of the Treaty (Official Journal of the EU L 187 of 26.06.2014, p. 1), hereinafter referred to as Regulation 651/2014/EU.
Therefore, in order to identify themselves in the appropriate group of entities, it is necessary to consider the indicated premises. Water supply companies qualify under the heading: Drinking water supply and distribution, i.e., entities that supply water for human consumption, including water supply and sewerage companies, as referred to in Article 2(4) of the Act of June 7, 2001 on collective water supply and collective sewage disposal (Journal of Laws of 2024, item 757), excluding entities for which the supply of water for human consumption is a non-essential part of the overall business.
The second item in the classification is Collective Sewage Disposal – entities that discharge or treat sewage, including water and sewerage companies, as referred to in Article 2(4) of the Law of June 7, 2001 on Collective Water Supply and Collective Sewage Disposal, excluding entities for which the discharge or treatment of sewage is a non-essential part of the overall business.
If an enterprise classifies itself into the above-mentioned groups of entities, it meets the first condition for inclusion in the National Cyber Security System (KSC) as a key entity. The next depends on the size of the enterprise. If a water and sewage enterprise meets the status of a medium-sized entrepreneur – it is recognized as a key entity. On the other hand, if it has the status of a large entrepreneur – it is recognized as a key entity . The scheme of considerations is shown in Figure 1.
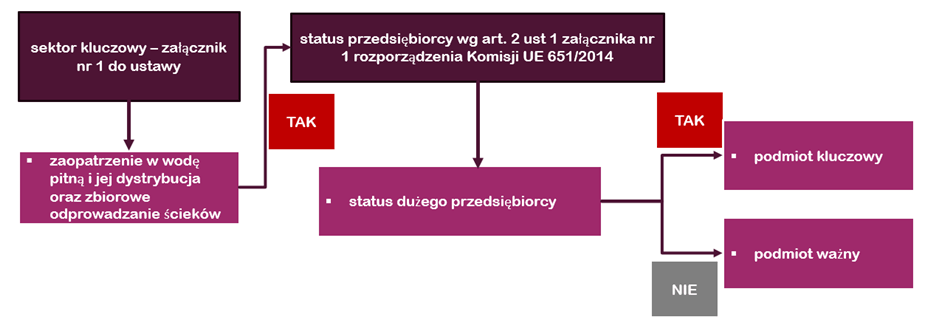
Key entity, important entity – responsibilities
In practice, qualification for the group of key or important entities actually differs little. In principle, the obligations arising from inclusion in the National Cyber Security System (NSC) for both types of entities are very similar. Only in the case of important entities are surveillance measures imposed only after a breach is detected (ex post). In addition, key entities will be subject to information security system audits.
The main obligation imposed by the bill on designated KSC units is to implement an information security management system (SBI). It requires, in addition to drafting, updating, archiving and, above all, applying documentation of continuous efforts to secure and monitor undesirable incidents, also their elimination and preventive response. KSC entities will be required to systematically estimate the risk of an incident, implement risk estimation and information system security policies, action plans to ensure the confidentiality, integrity, availability and authenticity of information and contingency plans, as well as cryptography policies and procedures, including encryption. So much for the theory.
On the technical side, KSC entities will be required to implement a continuous monitoring system (Security Operations Center – SOC), or “Cyber Command Center.” And here the financial and organizational question arises – who is to be responsible for this? Is a separate cyber security organizational unit, or an external unit professionally dedicated to cyber security? Both solutions have their advantages and disadvantages and probably as many supporters as opponents.
However, the choice requires a detailed analysis of security, organizational structure (including appropriately qualified human resources) and financial resources. Taking into account security issues, it is necessary to pay attention to the fact of possible sharing of IT/OT infrastructure with the entity externally, thus letting it into the entity’s own resources and systems to monitor and secure them remotely. This implies the need for appropriate contractual regulations and the implementation of prevention.
Another requirement imposed on KSC entities, and involving a real cost, is the obligation to conduct a security audit of the information system used to provide services by key entities, and submit the report to the relevant supervisory authority. Significantly, the KSC supervisory authority may also order an audit.
The head of the entity responsible for cyber security
According to the wording of the draft law on the KSC, as in the case of the regulations on the protection of personal data (RODO), the head of the key entity or major entity is responsible for fulfilling the obligations related to it. When the function is performed by a multi-member body and no responsible person has been designated, all members of the body are responsible.
What mobilizes most – possible penalties
What if an entity fails to meet its obligations or significantly violates them? According to the wording of the bill, heavy penalties will apply. Here it should be noted that, according to the assumptions, they may apply to the entity, but also to the head of the entity personally as responsible for cyber security.
How do digital security requirements relate to the security of the quality and quantity of water directed to consumers?
Water supply companies are obliged to comply with very strict requirements related to the quality of water directed to consumers. Regulations impose detailed obligations on the sector to monitor, treat and maintain water quality in the water supply network. In the era of digitalization, AI and the automation and computerization of water supply systems, it is impossible to limit water quality security solely to protecting infrastructure and monitoring physical parameters. There is a close connection between the cybersecurity of processes and the services provided – so vital to the health and lives of residents. Water supply systems are increasingly no longer just a pipe buried in the ground, but are widely developed systems full of automation, regulation, OT network connections and control. They are thus becoming potential targets for cyber-attacks that could threaten the health security of water.
In addition, as with the requirement to inform consumers about the quality of water supplied to them, key and important players will likely be required to provide the service user with access to knowledge to understand cyber threats and types of security.
Tick tock – October 17, 2024 behind us
Given that October 17, 2024 was the deadline for the implementation of EU regulations into national law and work is still ongoing – there is little time left to adapt to the new requirements. According to the announcements, the amendment to the KSC Law is expected to come into force within 1 month from the date of its promulgation (vacatio legis).Entities will have 6 months to comply with the new obligations and implement a safety management system, and 3 months to register in the list of entities covered by the KSC.
The challenges posed by new regulations and the requirements of the environment, regardless of the classification of the entity, will result in the need for financial outlays for the implementation of new solutions, as well as organizational (hiring of specialists) and training (training of staff) changes. And here, unfortunately, everything depends on the funds available to the entity.
A key issue in the implementation of cyber security in an entity is cooperation between IT departments, separate cyber security units, management and other organizational units of the entity – from the management level to the employee who is in no way associated with cyber security issues. Without proper awareness, backed by knowledge and, above all, interaction, it is impossible to implement and effectively manage a cyber security system to ensure adequate protection.
In the article, I used, among others. z:
- Draft Law on Amendments to the Law on the National Cyber Security System and Certain Other Laws dated 03/10/2024. https://mc.bip.gov.pl/projekty-aktow-prawnych-mc/902927_projekt-ustawy-o-zmianie-ustawy-o-krajowym-systemie-cyberbezpieczenstwa-oraz-niektorych-innych-ustaw.html
- Directive (EU) 2022/2555 of the European Parliament and of the Council of 14 December 2022 on measures for a high common level of cyber-security in the territory of the Union
- National Cyber Security Standards (NSC) https://www.gov.pl/web/baza-wiedzy/narodowe-standardy-cyber.
- National Institute of Science and Technology (NIST) https://www.nist.gov/
- Draft Digitalization Strategy of Poland https://www.gov.pl/web/cyfryzacja/strategia-cyfryzacji-polski-do-2035-roku

 Polski
Polski







